
Cyberattacks: You could be the next target
The surge of cybersecurity breaches in India has raised concerns, inviting calls for overhauling weak preventive systems, greater awareness and a stringent legal and regulatory framework
 With a significant spike in ransomware attacks, hackers are targeting companies of all sizes and sectors.
Image: Shutterstock
With a significant spike in ransomware attacks, hackers are targeting companies of all sizes and sectors.
Image: Shutterstock
On March 2, the Mumbai-headquartered Sun Pharmaceuticals reported that a security breach had taken place with its IT assets. On March 26, the company said its revenue is expected to decline as operations have been affected due to the attack.
If cybersecurity breaches can pull down India’s largest drugmaker, you could be next in line.
While Indian companies are riding the wave of rapid digitisation, the threat landscape is also expanding at an equally fast clip. India ranks third globally and first in the Asia-Pacific region in the list of 111 countries affected by the world-wide activity of scam groups distributing info-stealing malware, according to research by Group-IB, a Singapore-based cybersecurity firm. Another report by cybersecurity firm Palo Alto Networks points out that India is the second-most targeted country in the Asia Pacific and Japan region after Australia.
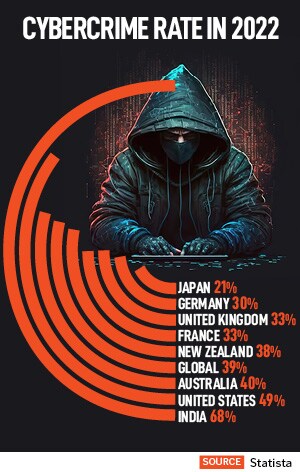
A study by Check Point Research, an American-Israeli cyber threat intelligence analyst, an organisation in India was attacked 1,866 times per week on an average in 2022, with the healthcare sector facing the maximum number of attacks.
Cyberattacks have surged over the years because they have become a successful financial model, explains Dmitry Volkov, CEO and co-founder of Group-IB. “We see the threat actors evolving continuously every year. The number of cybercriminals who manage this ransomware activity and affiliate programmes continues to grow. That's why, because of high competition, they're always trying to learn new ways to earn money from new regions. The whole ecosystem of threat actors continues to develop. They don't rely on one single group, they attack simultaneously, on multiple companies.”




 The regulatory landscape is quite weak in India. If there is a cyberattack or data breach, there aren’t any significant fines or disincentives for the companies to invest more in cybersecurity, explains Yash Kadakia, founder of Security Brigade, an information technology security solutions provider.
The regulatory landscape is quite weak in India. If there is a cyberattack or data breach, there aren’t any significant fines or disincentives for the companies to invest more in cybersecurity, explains Yash Kadakia, founder of Security Brigade, an information technology security solutions provider. 
 Threat intelligence has existed for many years, but the companies don’t use this knowledge, says Volkov of Group-IB. He adds that there is lack of human resources. “If you talk about knowledge, you must have at least a few people in the company who will be able to convert knowledge in some actions to protect the organisation. Post the pandemic, a lot of people are working remotely. And these are very easy to compromise. Another very important thing is ‘passwords’. It all starts from there, using the same passwords for different logins can be an easy target for the attackers. Even if you use two-factor authentication, it is still possible to bypass it. So resusing and having the same passwords should be avoided,” he says.
Threat intelligence has existed for many years, but the companies don’t use this knowledge, says Volkov of Group-IB. He adds that there is lack of human resources. “If you talk about knowledge, you must have at least a few people in the company who will be able to convert knowledge in some actions to protect the organisation. Post the pandemic, a lot of people are working remotely. And these are very easy to compromise. Another very important thing is ‘passwords’. It all starts from there, using the same passwords for different logins can be an easy target for the attackers. Even if you use two-factor authentication, it is still possible to bypass it. So resusing and having the same passwords should be avoided,” he says. 




