Traceability and end-to-end encryption cannot co-exist on digital messaging platforms: Experts
In the first of a two-part series, Forbes India explores how enabling identification of the source of viral messages in end-to-end encrypted platforms is likely to have a chilling effect on free speech, while not successfully curbing the spread of misinformation
 Image: Shutterstock; Illustrations: Sameer Pawar
Image: Shutterstock; Illustrations: Sameer Pawar
The Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021, which the government of India notified on February 25, were supposed to provide clarity on whether or not breaking end-to-end encryption is a limit that platforms must breach to enable traceability. Instead, even two weeks after the Rules have been notified, there is no clarity on what they mean for end-to-end encrypted messaging platforms.
Much of the debate around “enabling the identification of the first originator” or traceability on end-to-end encrypted platforms has circled around whether it is possible to identify the originator of a message without breaking or diluting end-to-end encryption. So much so that a crucial case on enabling traceability on WhatsApp, which got transferred to the Supreme Court from the Madras High Court, spent at least four hearings discussing whether or not traceability was possible without breaking end-to-end encryption. In the last hearing in January 2020, notification of these Rules was still awaited. The case is still pending.
The Indian government has maintained that it is indeed possible. However, WhatsApp, Signal, privacy advocates and other cryptography experts have vehemently said that enabling identification of the originator at the very least defeats the purpose of end-to-end encryption if not entirely breaks it.
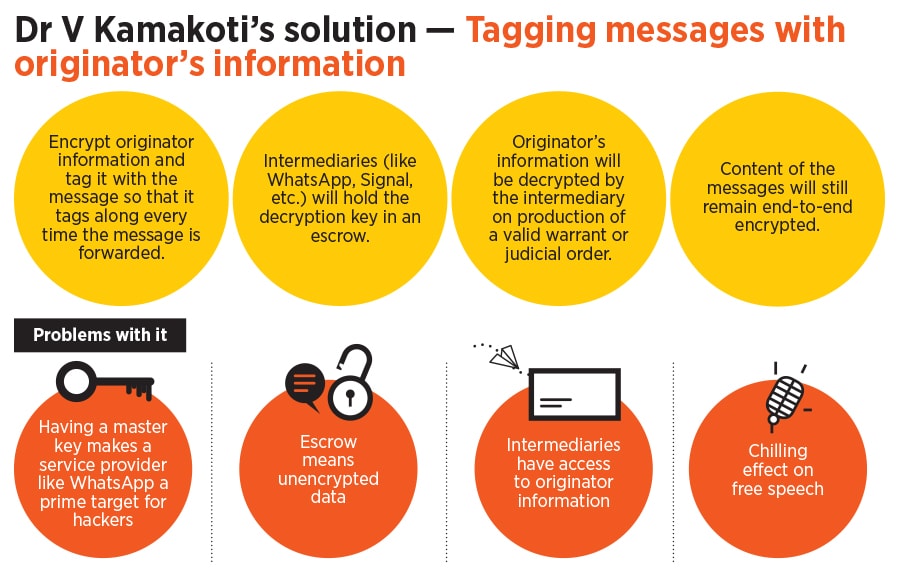
The Indian government has thus far been proposing two schemes as potential solutions to the problem of identifying the originator: Tagging each message with the originator’s information (as proposed by IIT Madras’s Dr V Kamakoti); and comparing hash values of problematic messages with what WhatsApp/intermediary has (as discussed by Rakesh Maheshwari from the Ministry of Electronics and Information Technology [MeitY] at multiple public events).
Moxie Marlinspike, creator of the Signal protocol and CEO of Signal Messenger, told Forbes India a fortnight before the Rules were notified that “Signal is designed so that Signal does not know who is messaging who. Signal doesn’t have that information.” On traceability, he said that end-to-end encryption and traceability cannot co-exist. “There is no way to have data privacy for everybody but just a specific set of people. [Once you make it possible] to just give the police access to data under some set of circumstances, anyone can get access to that data.”





 A bigger problem is that storing a master key for the originator information makes WhatsApp a prime target for hackers and defeats the purpose of data minimisation.Forbes India has a copy of WhatsApp’s submission.
A bigger problem is that storing a master key for the originator information makes WhatsApp a prime target for hackers and defeats the purpose of data minimisation.Forbes India has a copy of WhatsApp’s submission.