
- Home
- UpFront
- Take One: Big story of the day
- Can traceability and end-to-end encryption co-exist? Here's the legal view
Can traceability and end-to-end encryption co-exist? Here's the legal view
In the first part of our deep dive into the government's new IT rules, we examined, from the technological point of view, why implementing traceability on end-to-end encrypted social media platforms will erode privacy and increase misinformation. In the second part, we now look at the legal challenge of implementation and the potential contradictions

Aditi covers technology, privacy, surveillance and cybersecurity. You can send tips at aditi.agrawal@nw18.com or at mail.aditi@pm.me. Email for Signal/WhatsApp details.
- West Bengal considering state legislation to act against apps like Sulli Deals: Derek O'Brien
- Parliamentary panel's version of Personal Data Protection Bill endangers privacy: Justice Srikrishna
- BJP MPs successfully thwart attempts to discuss Pegasus issue in IT Parliamentary Committee
- Overview: Facebook, Twitter, Google and Koo file first compliance report under new IT Rules
- PTI sues Centre, calls digital media code state's 'weapon' to control media
- Mobile internet services suspended in most of Haryana until January 30
- Traceability and end-to-end encryption cannot co-exist on digital messaging platforms: Experts
- 'Poorly planned, India not ready for 5G deployment'
- PTI sues Centre, calls digital media code state's 'weapon' to control media
- Facebook, WhatsApp sue Indian government over traceability requirement
 Image: Shutterstock
Image: Shutterstock
Every time we talk about end-to-end encryption and traceability, two questions arise: Is traceability, that is, immediately getting to the first person who sent a message that has been forwarded multiple times, technologically possible while preserving end-to-end encryption? And the bigger question is: Should it be made possible?
The Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021, that were supposed to be notified by January 15, 2020, were meant to provide clarity about these two questions. However, discussions with both legal and technical experts prove otherwise. Despite being notified more than a year later on February 25, 2021, with significant changes that had not been publicly consulted upon, the new rules are proving to be quite polysemous.
WhatsApp has long argued that enabling traceability means “lowering the wall” of privacy and security for everyone. It is still not clear if the new Rules lower the wall, that is undermine end-to-end encryption to get to the “first originator”. Cryptographic experts, however, are clear that traceability and end-to-end encryption cannot co-exist.
Traceability is not a new demand—neither by the Indian government nor by any other government in the world. It has often been accompanied by a demand for removing objectionable content from the platform.
What kind of services does the traceability rule cover?
Rule 4(2) mandates all significant social media intermediaries, that is social media platforms with more than 50 lakh users, “providing services primarily in the nature of messaging” to enable the identification of the first originator.
Messaging services such as WhatsApp, Signal, iMessage are clearly covered. The government’s own end-to-end encrypted app, Sandes, built on top of the Government Instant Messaging System (GIMS) would have to enable traceability, if it has more than 50 lakh users in India. “If WhatsApp is a social media intermediary, then an entity which undertakes an enterprise similar to WhatsApp is a social media intermediary,” says Priyadarshi Banerjee, a Supreme Court lawyer who has also represented Twitter in the WhatsApp traceability case. Forbes India has reached out to the National Informatics Centre (NIC) to understand how the Sandes app will enable traceability while retaining end-to-end encryption. Interestingly, since the notification of the rules, the FAQs on the Sandes website have been taken down.
However, it gets murkier when it comes to public social media platforms whose primary services are arguably not messaging. Neither the Rules nor the Information Technology Act, 2000, define what messaging is. Traceability is not much of a problem on open and public platforms such as Facebook, Twitter, Instagram, LinkedIn, YouTube, and most email service providers, as all of them retain information about what is posted, when it is posted, who posted it, and the IP address it is posted from, a fact that Twitter had submitted in a case before the Madras High Court in 2019.
“Is Twitter primarily a messaging service? Would it have to trace when a DM [direct message] was first sent in India?” asks Udbhav Tiwari, public policy advisor at Mozilla. “To what extent would a service like Dunzo or Zomato, whose primary function is not messaging, have to enable traceability?” he wondered. Going ahead with this logic, does it then mean that if a social media intermediary is primarily not a messaging service, it can implement E2EE without enabling identification of the originator?
It is a problem for end-to-end encrypted services such as WhatsApp, Signal, iMessage, secret chats on Telegram and Facebook Messenger, and others.
Can the Rules break encryption? Do the Rules break encryption?
All experts that Forbes India spoke to agreed that the government has not categorically asked for breaking E2E encryption; it has just defined the information it wants—the first originator’s—without defining the method. However, functionally, they may undermine E2E encryption.
The provisions that have been used to notify the Rules only deal with the general rulemaking powers of the Central Government, the procedure for blocking access to internet resources under Section 69A, and the guidelines that intermediaries need to observe under Section 79(2). They do not deal with encryption.
“Section 87(2)(zh) refers to the government’s power to prescribe modes or methods of encryption. If at all, what is contained in the Rules has a bearing on what kind of encryption the platforms can or cannot implement, and if it will impact their technical architecture, I don’t believe it would be done legally through these rules because the rules don’t mention (zh) or Section 84A. The Rules are trying to do indirectly what could have been done directly under this provision,” says Gunjan Chawla, programme manager for Technology and National Security at NLU Delhi’s Centre for Communication Governance. Gurshabad Grover, a senior researcher at the Bengaluru-based Centre for Internet and Society, explains that as per case law, delegated legislation cannot infringe upon fundamental rights if the parent act does not foresee such invasion. Since “Section 79 of the IT Act, under which these Rules have been notified, does not allow for any invasion of privacy”, “any rule that leads to invasion of privacy is already exceeding the scope of what is allowed by the parent Act”, he says.

Grover also pointed out that compared to the draft amendments related to traceability, the language is much more tempered in the notified Rules. “I think the Ministry is making a genuine attempt to signal to services that they are not required to break end-to-end encryption,” he said.
Do the Rules prevent other companies from introducing E2E encryption?
There is another rule, Rule 3(1)(k), which applies to all intermediaries that forbids them from “knowingly” deploying or modifying the technical configuration of their systems which “may change or has the potential to change the normal course of operation of the computer resource that what it is supposed to perform thereby circumventing any law”. While this rule had been notified in 2011, it may have a bearing on future implementation of E2E encryption if the encryption is incapable of identifying the originator.
For instance, Google is currently in the process of rolling out end-to-end encryption by default for Android messages. Will Rule 3(1)(k) mean that Google is trying to circumvent the traceability requirement and thus cannot implement end-to-end encryption? Does this forbid Facebook from enabling default E2E encrypted messenger services on Facebook Messenger and Instagram Messenger? Banerjee says this will be a test for application for Rule 3(1)(k). “But practically, for a court, it will be very difficult to rule that if you already had E2EE on February 25, you are not in circumvention of the Rule but if you implement it after February 25, you are in circumvention,” he warns.
Banerjee also explained that Rule 3(1)(k) is not as much about E2E encryption as it is “about ensuring that a company does not keep changing its source code to look like another company”. One application could be to act against mirror sites that host pirated content. Nikhil Narendran, partner at the law firm Trilegal, explained that Rule 3(1)(k) was actually introduced to regulate companies that scan computers for anti-virus and ransomware. “At that time, end-to-end encryption was not really a consideration,” he says.
Grover also points out that regardless of Rule 3(1)(k), there is a problem. “One way is to ban it [E2E encryption] and one way is to disincentivise it so much that it is no longer for companies to deploy it,” he says. “Knowing that there is a traceability requirement, why would an Indian company implement the Signal protocol [which is open source] which cannot enable traceability?” he asks.
When it comes to dismantling E2E encryption, it is not just the Intermediary Rules. There is confusion around Rule 13(3) of the existing IT (Procedure and Safeguards for Interception, Monitoring, and Decryption of Information) Rules, 2009 as well. Rule 13(3) defines “decryption assistance” as “any assistance to (i) allow access, the extent possible, to encrypted information; or (ii) facilitate conversion of encrypted information into an intelligible form”.
In the Supreme Court in 2019, Attorney General KK Venugopal, on behalf of Tamil Nadu, had argued that the this Rule, paired with Section 69(3) of the IT Act, means that the intermediary must do everything to assist the law enforcement agency, even if it means breaking encryption. Mukul Rohatgi, on behalf of Facebook, had argued that in absence of a decryption key, there is nothing that Facebook can do and thus decryption or re-architecting the platform is not on the table.
Banerjee and Narendran both agree with Rohatgi’s argument. “If you have it, you give the solution. If you don’t, you don’t. I think it is the intermediary’s right that ‘to the extent possible’ means to the extent possible as the platform stands today,” says Banerjee. “To my mind, unless there is another law that says that you must do this or you cannot do this, the Section 69 Rules don’t require companies to re-architect their platforms,” says Narendran.
The demand for traceability in India
In India, questions were first raised around WhatsApp’s end-to-end encryption in 2018. Fuelled by rumours on WhatsApp, violent mobs across India had lynched and killed multiple people. The only way for law enforcement agencies to get to the person who starts a malicious rumour or engages in hate speech is to manually go back each message. Thus, if a message is forwarded 100 times, the police have to manually trace at least a 100 people. And if one person has deleted the message, it breaks the chain.
There is currently at least one case in the Supreme Court, which was transferred from the Madras High Court, where the question of traceability is under consideration. It is not clear if this case, called the WhatsApp traceability case, will turn infructuous. Banerjee says that since the solution for traceability is not there, the case will continue, though the submissions to the court may have to be amended. “As long as WhatsApp is party in the case, the case will not come to an end,” he says.
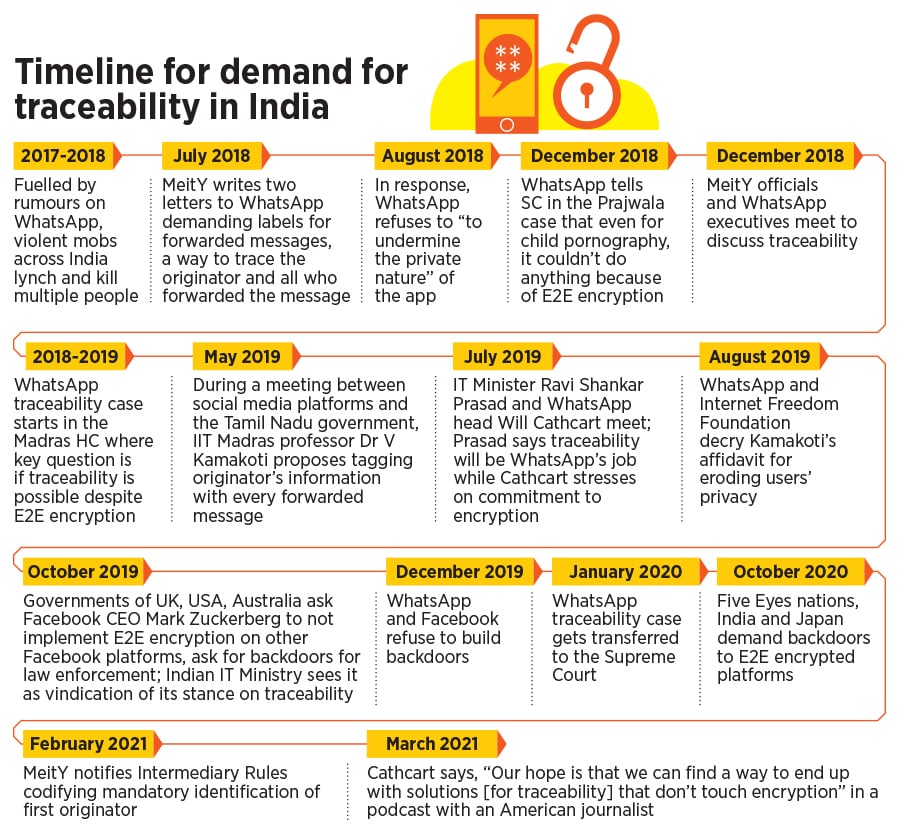
Law enforcement agencies welcome the traceability requirement
Welcoming the rules in general, Anyesh Roy, the deputy commissioner of police who heads Delhi Police's Cyber Crime Cell unit, told Forbes India that a number of provisions within the Rules are helpful for law enforcement agencies.

Roy, who gave inputs to the formulation of the Rules, makes it clear they don’t ask for breaking E2E encryption. Reiterating the proposal of IIT Madras’s V Kamakoti to tag originator information with every forwarded message in the metadata, that is, data outside of the content of the message itself, he said. “Stamping the originator's information in the message metadata will help law enforcement trace messages linked to fake news and violence," he said.
Lawyers, on behalf of Tamil Nadu, during the WhatsApp traceability case had said that they want some semblance of traceability that can aid the police in investigating crimes, as well as greater cooperation from social media platforms. Balaji Srinivasan, the additional advocate general for Tamil Nadu, who represented the state in the case, welcomed the Rules and said they “address the long-standing demand of law enforcement agencies to make information of offenders available to it for solving sensitive, sensational, horrific, dreadful and terrible crimes”. He said the Rules do not break E2E encryption as they do not require any information except the metadata of the message to be disclosed.
However, Grover and Dr Debayan Gupta, an assistant professor of Computer Science at Ashoka University, both point out the metadata is data. “If I get a call from a pathology lab and then call an oncologist, even without knowing the content of my conversation, you can conclude what the conversation was about,” Gupta said. Grover reminded that in a debate in 2014, General Michael Hayden, the former director of the CIA and NSA, had said, “We kill people based on metadata.”
“Only with metadata, what am I going to do? Tomorrow, if someone has uploaded child porn, unless and until I have content, what do I say?” asks Brijesh Singh, inspector general of Maharashtra Police (Cyber). While metadata is essential for investigation, law enforcement agencies require content to submit as evidence. Arguably, once content on an E2E encrypted platform is reported, at least one “end” will have to be shown to the law enforcement agency. “You cannot create an invisibility cloak and use it for committing crimes,” he says.
Singh calls the fear of the Rules diluting the anonymity offered by E2E encryption, if not entirely undermining it, “a figment of imagination”. “There are technological means which are available which only talk about the time stamp,” he says. He suggested solutions that could be akin to blockchain technology where time stamps of transactions are visible even if the transaction itself remains encrypted.
WhatsApp’s “Forwarded” labels, which were introduced after repeated demands by the Indian government to tackle misinformation, have ironically coloured discussion about WhatsApp’s abilities. While announcing the notification of the Rules, IT Minister Ravi Shankar Prasad had said that by virtue of being able to add “Forwarded” and “Forwarded Many Times” (denoted by a double arrow) labels to messages, WhatsApp is able to track certain messages. The same argument was made by both Roy and Singh.
However, when it comes to the “Forwarded” label, there is nothing that is done on the WhatsApp server. It is the app client on the user device that adds the “Forwarded” label when a user selects the “Forward” button. These forwarded messages, WhatsApp explains, contain a counter that tracks how many times a message is forwarded but WhatsApp itself is not privy to this information.
But at least one law enforcement officer has a different perspective. At an online event and in an opinion piece for The Business Line, Yashovardhan Azad, former special director of the Intelligence Bureau, warned that undermining end-to-end encryption via traceability also means jeopardising the government’s own methods of communication.
Less than a week after the Indian government notified the Rules that direct messaging platforms with more than 50 lakh users to “enable identification of the first originator”, FBI Director Christopher Wray, while testifying about the investigation into the insurrection at the US Capitol on January 6, told the Senate Judiciary Committee that end-to-end encryption, especially when it is by default, prevents law enforcement agencies from getting access to information “no matter how bulletproof or ironclad the legal authority”.
Wray’s statement echoes what Roy had said in November about E2E encryption: “So that impossibility [of getting access to information on an E2E encrypted platform] basically nullifies the provision of law which has been provided for by the Parliament of India.”
Wray, in his prepared remarks, too said that the FBI is not asking for backdoors, echoing the Indian government’s claims that they are not asking to break E2E encryption. But if the information they require mandates breaking it, isn’t that essentially what they are asking for?
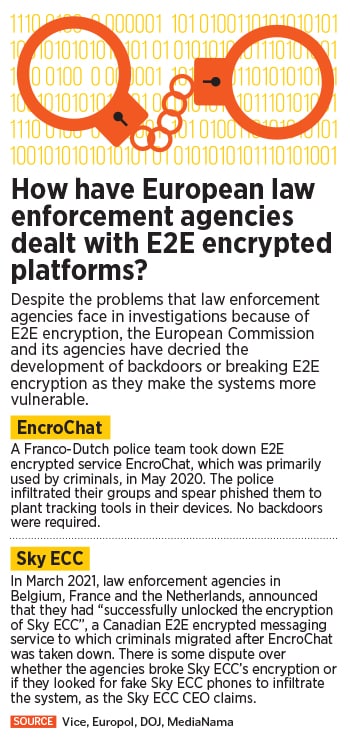
What kind of data do WhatsApp and Signal have?
In a submission to the Madras High Court, WhatsApp had said that it gives basic subscriber information to law enforcement agencies. This includes phone number, name, device information, app version, start date/time, connection status, last connection date/time/IP, email address, and web client data. WhatsApp also has information about all the contacts of a user, names of all the groups they are part of, but the Madras HC submission did not include those.
Signal turns over only the date on which the account was created and the last connection date because it does not collect any other data. It is not clear what all records are included in an Account Preservation Request that law enforcement agencies submit to WhatsApp. Forbes India has reached out to WhatsApp for clarification.
Is the originator the perpetrator?
Roy, in an interview, had earlier said that the metadata provided by WhatsApp is enough to get to the perpetrator but not the originator. On asking what happens when a message causes problems if it is forwarded without context and vilifies the originator needlessly even if malice was intended by a subsequent recipient, Roy says, “The investigation will bring that out and you will not face any problem because of that if the log will be there in your device so you can always give this explanation.”
When it comes to establishing whether the originator is a perpetrator of a crime, that does not fall within the ambit of the Rules. Chawla explained that Indian Penal Code sections related to criminal conspiracy would have to be invoked to charge the perpetrator. Banerjee explained that when it comes to originator, “they are looking at the users who are sitting at the ends of the terminal”, not the person at whose behest the message is sent. The courts will need context to convict a person so that is not necessarily a shortcoming within these Rules, he explained.
How do you determine the first originator within India?
There is a curious proviso in the Rules that has caused much consternation. As per it, when the first originator of the message is located outside India, the first person who shares the message within India will be considered the first originator. Thus, if a message was sent from the US to a person in India, if this recipient forwards it, they will be considered the first originator.
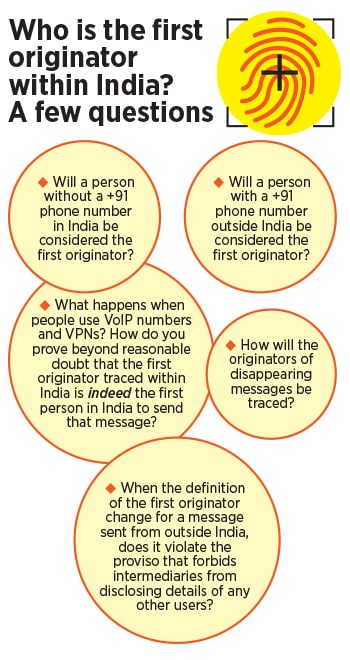
In a conversation with Forbes India, Kamakoti suggested that the E2E encrypted platforms could use GPS information to ascertain whether the first originator was in India or not. On asking whether this would mean tracking people’s locations and disabling the ability of users to choose to share location data with the app, he said, “We are not asking for the GPS information. We just use the GPS value to find out whether they are in India or not.” He clarified that this is not the only way it can be done.
Kamakoti’s idea is that the intermediary should ascertain the latitude and longitude values through the GPS receiver on the phone instead of the location sharing feature on these apps. Through this data, the intermediary will determine if the user was within India at the time of sending the message and then label the user as the first originator if the message came from outside India.
The privacy implications of determining the location of each user in this manner cannot be overstated. Moreover, spoofing GPS locations on the phone is quite literally child’s play, as Gupta pointed out. In response to Forbes India’s question about this, Kamakoti said, “We should make a resilient software that does not enable this. This is the way we build systems. Everywhere, everything can be faked. How does security build? You make more robust systems. This is one way.”
Graphics by Sameer Pawar




